The content filter field allows you to filter and process events based on their event message text. Content filtering distinguishes between the following:
•Wildcard match of the entire event message (default)
•Insertion string match
•Regex match (Perl syntax)
Wildcard Match
With this option, the specified text will be matched against the entire event message text (aka event description). You can either use wildcards in your content filter, or specify a 1:1 match.
Insertion String Match
Most events that are logged to the event log and contain dynamic information contain one or more insertion strings (click here for a detailed discussion on event message files and insertion strings). While a basic wildcard match is sufficient in most cases, the insertion string match gives you the following benefits:
1.No complex queries have to be crafted in order to match a subset of the event message
2.Additional comparison types (e.g. numerical) are available for insertion strings
With the insertion string match, you can not only perform textual comparisons of insertion strings, but also the following:
1.Numerical comparison (less than, equal, not equal, more than)
2.File checksum comparison
3.Group membership check
Using insertion string variables (e.g. $STR2) in the Content Filter field is supported and allows for insertion strings to be compared with each other at run time.
1. Numerical comparisons
When you select one of the numerical comparisons for an insertion strings, then EventSentry will convert the textual insertion string to a number, and then perform the select numerical comparison on that string. Numerical comparison supports floating point numbers.
Note: Only use this option if the insertion string is a number.
2. File checksum comparisons
Treats an insertion string as a filename, and creates a SHA-256 checksum of the file. The checksum you specify is then compared with the checksum of the file.
|
Only use this options 2 and 3 if the insertion string points to a file name. Do not use this option with events that occur at a high frequency or with insertion strings that point to large files, as checksum generation may use a significant amount of CPU time. |
3. File entropy comparisons
Similar to the checksum comparison, treats an insertion string as a filename and calculates the entropy (randomness) of a file. The entropy is returned as float number with a range from 0 to 10. The more random a file, the higher its entropy. This can be used to detect a Ransomware outbreak which creates a large number of files with a high entropy. In practice, compressed and encrypted files have a high entropy.
You can check the entropy of a file with the /e option of the "checksum.exe" utility of the EventSentry SysAdmin Tools.
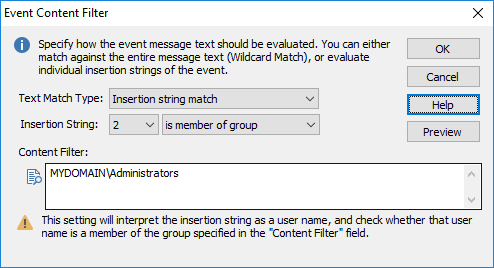
4. Group membership check
Treats the insertion string as a username, and verifies whether the username is a member of the group you specify. To avoid ambiguity, it is recommended that specify group names with the domain or host name, for example DOMAIN\GroupA or SERVERB\GroupX.
|
Only use this option if the insertion string points to a valid username. Do not use this option with events that occur at a high frequency, as group verification may be time consuming (relatively speaking) and use large amounts of CPU time. |
5. Malicious IP Address Check
Checks whether an IP address from an event log event is listed in any of the downloaded blacklists (also checks AbuseIPDB if configured). The filter will only match if the IP address is deemed malicious. Only works for collector-enabled actions, since the IP address check is performed on the collector (and not at the agent). Requires that Threat Intel is enabled.
6. Wildcard comparison ("matches")
Similar to the wildcard match, but this option matches the selected insertion string against the specified text.
7. Command line arguments
Counts the number of command line arguments contained in a string, taking quotes etc. into consideration, allowing to filter if the number of arguments are fewer than, equal to or exceed a certain count. This can be useful for detecting certain malware or other anomalies.
8. Geo IP Country match
Resolves the country that is associated with the IP address, specify the two-letter country code (left column) (e.g. AT, IT, US). Only works for collector-enabled actions, since the IP address check is performed on the collector (and not at the agent). Requires that a GEO location IP database is present and configured (supplied & enabled by default). A filter can either match if an IP matches a country or does not match a specific country code.
If both an event source and event id are specified in the filter properties and the message file is correctly registered, then the Preview button can be used to see the event template and its insertion strings. The event message browser can also show the available insertion strings of an event.
The table below shows the types of strings expected by the individual comparisons:
Match Category |
Expected type of string in "Content Filter" |
matches |
any string |
matches file checksum |
Filename with complete path |
is member of group |
Username |
numerical |
any number |
Supports case insensitive text matching based on regular expressions. EventSentry uses the PCRE engine, please see Regular Expressions for the complete syntax.
The most common regular expression metacharacters are:
^ |
matches the beginning of the event message text |
$ |
matches the end of the event message text |
. |
matches any characters |
\s |
matches a whitespace character |
\d (\D) |
matches a decimal digit (non-digit) |
\ |
quote the next metacharacter |
[] |
sequence, e.g. [a-z] matches all lowercase letters from a-z |
|
Since an event message text will often consist of more than one line, the ^ symbol will always match the beginning of the event message, even if the event contains multiple lines. Equally, the $ symbol will always match the end of the entire event message text, and not the end of the first line. |
In addition, regular expressions support the following quantifiers:
* |
match 0 or more times |
+ |
match one or more times |
? |
match 1 or 0 times |
{n} |
match n times |
{n,} |
match at least n times |
{n,m} |
match at least n times, but no more than m times |
The table below shows basic regular expression examples:
Text |
Matching regular expression |
Opera 11.61 (Opera Software ASA) was installed. |
^Opera\s\d\d\.\d+.*installed.$ |
Computer TEST3-WIN2K8 booted. |
^.*TEST\d-WIN\dK\d.*$ |
User RENAULT\francois3 logged on. |
^User\s[A-Za-z]+\\[A-Za-z0-9]+ logged on.$ |
You can use the negation character (exclamation mark, !) for any text-based matching. Please see Advanced Text Processing for more information.
